Configuring Istio Ingress with AWS NLB
Ingress AWS Network Load Balancer
This post provides instructions to use and configure ingress Istio with AWS Network Load Balancer.
Network load balancer (NLB) could be used instead of classical load balancer. You can see the comparison between different AWS loadbalancer for more explanation.
Prerequisites
The following instructions require a Kubernetes 1.9.0 or newer cluster.

nlb on kubernetes is an alpha feature and not recommended for production clusters.
IAM Policy
You need to apply policy on the master role in order to be able to provision network load balancer.
-
In AWS
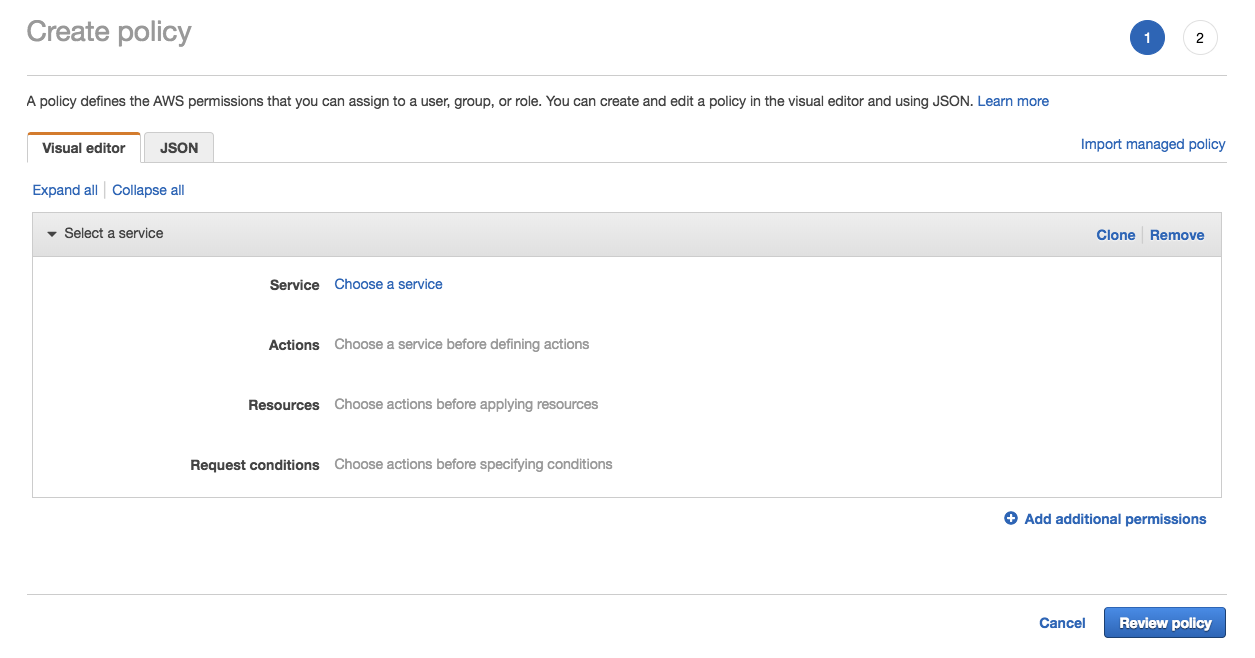
iamconsole click on policies and click on create a new one:Create a new policy -
Select
json:Select json -
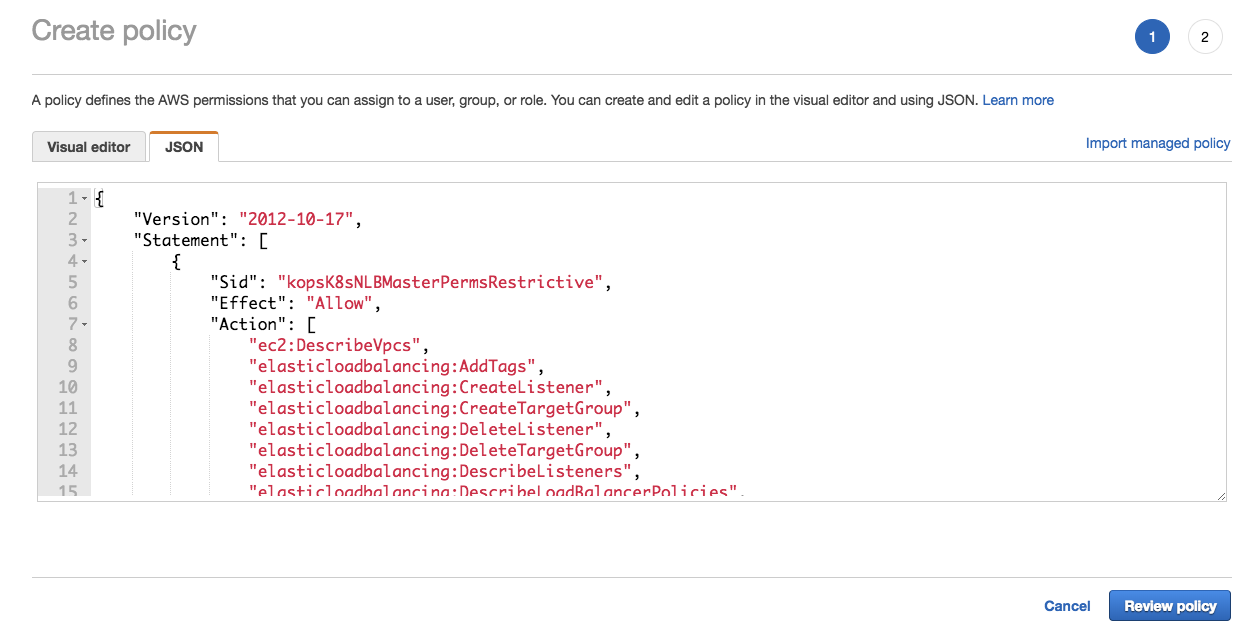
Copy/paste text below:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "kopsK8sNLBMasterPermsRestrictive", "Effect": "Allow", "Action": [ "ec2:DescribeVpcs", "elasticloadbalancing:AddTags", "elasticloadbalancing:CreateListener", "elasticloadbalancing:CreateTargetGroup", "elasticloadbalancing:DeleteListener", "elasticloadbalancing:DeleteTargetGroup", "elasticloadbalancing:DescribeListeners", "elasticloadbalancing:DescribeLoadBalancerPolicies", "elasticloadbalancing:DescribeTargetGroups", "elasticloadbalancing:DescribeTargetHealth", "elasticloadbalancing:ModifyListener", "elasticloadbalancing:ModifyTargetGroup", "elasticloadbalancing:RegisterTargets", "elasticloadbalancing:SetLoadBalancerPoliciesOfListener" ], "Resource": [ "*" ] }, { "Effect": "Allow", "Action": [ "ec2:DescribeVpcs", "ec2:DescribeRegions" ], "Resource": "*" } ] } -
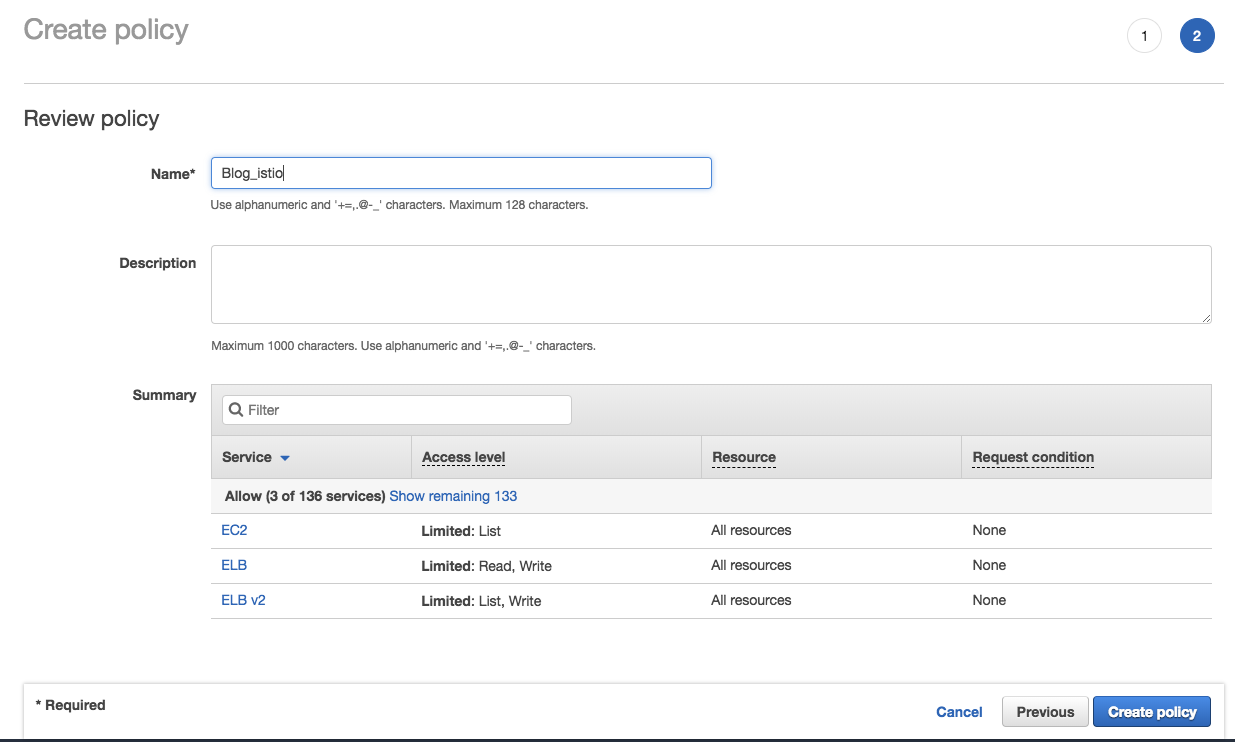
Click review policy, fill all fields and click create policy:
Validate policy -
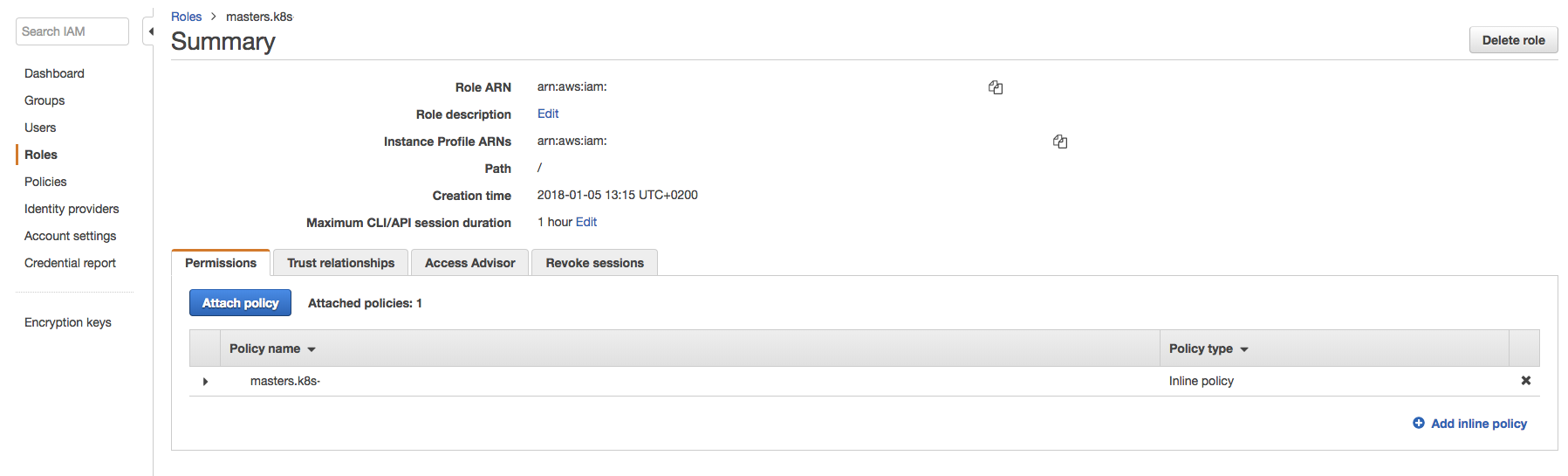
Click on roles, select you master role nodes, and click attach policy:
Attach policy -
Your policy is now attach to your master node.
Rewrite Istio Ingress Service
You need to rewrite ingress service with the following:
apiVersion: v1
kind: Service
metadata:
name: istio-ingress
namespace: istio-system
labels:
istio: ingress
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
spec:
externalTrafficPolicy: Local
ports:
- port: 80
protocol: TCP
targetPort: 80
name: http
- port: 443
protocol: TCP
targetPort: 443
name: https
selector:
istio: ingress
type: LoadBalancer
What's next
Kubernetes service networking should be consulted if further information is needed.